Top 10 Cloud Security Services Comparison
By Sheila Morgan | Published: 2025-02-21 | Category: Cloud Security Services
About Cloud Security Services
Cloud security services provide specialized tools and technologies to protect cloud-based infrastructure, applications, and data against threats and ensure compliance. They address vulnerabilities, manage identities, prevent data loss, and monitor cloud environments for malicious activity.
Scoring Criteria
- → Threat Detection & Prevention
- → Compliance & Governance
- → Visibility & Control
- → Integration Capabilities
- → Scalability
- → Ease of Use
- → Support & Documentation
- → Pricing & Value
The Best Cloud Security Services
 #10
#10
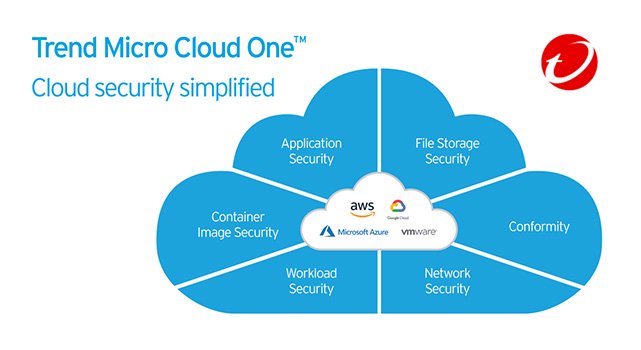
Trend Micro Cloud One
By Trend Micro
A broad security services platform offering multiple security capabilities for cloud builders, including workload, network, container, file storage, and application security.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, VMware, Containers, Serverless
Best For: CWPP, Network Security, Container Security, File Storage Security, Application Security, CSPM, Open Source Security
Key Features
- ✓Modular Platform: Offers specialized services like Workload Security, Container Security, Network Security, etc.
- ✓Deep Security Heritage: Builds on Trend Micro's long-standing expertise in workload and network protection.
- ✓Strong Integration with Cloud Providers: Connects well with native cloud services and marketplaces.
- ✓Flexible Deployment: Offers SaaS and self-hosted deployment options for some components.
Scorecard (Overall: 7.4 / 10.0)
Pricing
Free Tier
Contact Vendor
- Limited access to Conformity (CSPM)
- Basic container scanning
Pay-as-you-go / Annual Subscription
Contact Vendor
- Pricing per module (e.g., Workload Security per instance-hour)
- Conformity based on resources
Limitations: Pricing can be complex due to modularity, Multiple consoles historically, though unifying
Pros
- + Broad range of security services on one platform
- + Strong workload protection features
- + Flexible pricing models (incl. PAYG)
- + Good reputation and support
Cons
- - Platform can feel somewhat disjointed due to its modular nature
- - Interface can be complex
- - Some modules stronger than others
Verdict
"A comprehensive suite from a security stalwart, offering flexibility through its modular approach, suitable for organizations needing diverse cloud security tools under one vendor."
 #9
#9
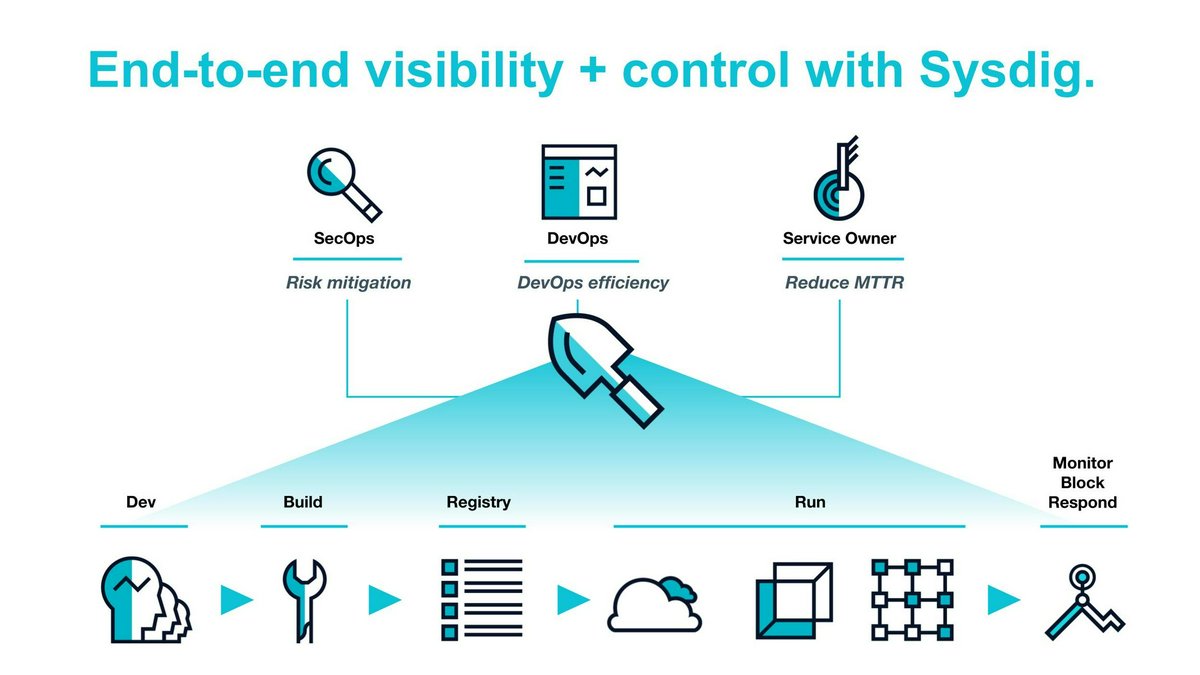
Sysdig Secure
By Sysdig
Focuses on securing the software build pipeline and providing runtime threat detection for containers, Kubernetes, and cloud services.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, Containers, Linux
Best For: CWPP, Container Security, Kubernetes Security, CSPM, Compliance, Runtime Threat Detection
Key Features
- ✓Deep Container Visibility: Leverages Falco open-source engine for runtime threat detection based on system calls.
- ✓Kubernetes Security Posture Management (KSPM): Specialized checks and controls for Kubernetes environments.
- ✓Image Scanning & Admission Control: Scans container images for vulnerabilities and enforces policies before deployment.
- ✓Compliance Frameworks: Supports standards like PCI, NIST, SOC 2 for cloud and container environments.
Scorecard (Overall: 7.5 / 10.0)
Pricing
Essentials
Contact Vendor
- Core security features for containers and cloud
Secure
Contact Vendor
- Full platform capabilities including compliance, advanced threat detection
Limitations: Contact vendor for pricing, Primarily agent-based
Pros
- + Excellent runtime security for containers and Kubernetes
- + Strong open-source foundation (Falco)
- + Good integration into DevOps workflows
- + Detailed forensics capabilities
Cons
- - Primarily focused on containers/Kubernetes
- - CSPM capabilities less extensive than leaders
- - Can have a steeper learning curve
Verdict
"A top choice for organizations prioritizing deep security for containerized and Kubernetes environments, particularly runtime threat detection."
 #8
#8
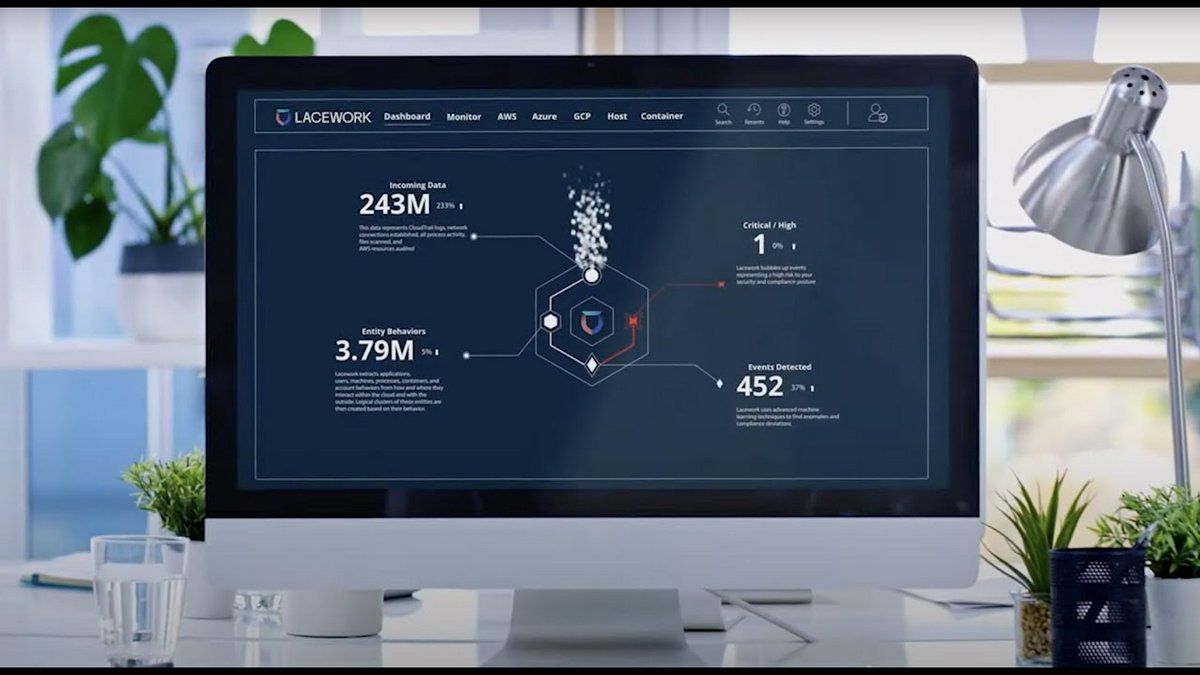
Lacework Polygraph Data Platform
By Lacework
A data-driven cloud security platform using behavioral analytics and machine learning to detect threats, misconfigurations, and vulnerabilities.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, Containers, Workloads
Best For: Threat Detection, CSPM, CWPP, Compliance, Vulnerability Management, Container Security
Key Features
- ✓Behavioral Anomaly Detection: Uses machine learning to baseline normal activity and detect deviations indicating threats.
- ✓Polygraph Visualization: Maps cloud entities and activities to provide context around alerts.
- ✓Agent & Agentless Options: Offers flexibility for data collection across infrastructure and workloads.
- ✓Continuous Compliance Monitoring: Checks against standards like CIS, SOC 2, PCI DSS.
Scorecard (Overall: 7.5 / 10.0)
Pricing
Custom Quote
Contact Vendor
- Based on cloud resources monitored
- Tiered feature sets
Limitations: Pricing not publicly available, ML-based approach can sometimes generate noise
Pros
- + Innovative behavior-based threat detection
- + Good visualization for understanding context
- + Combines CSPM and CWPP
- + Scalable data platform
Cons
- - Anomaly detection may require tuning
- - Can be alert-heavy initially
- - Relatively newer player compared to some giants
Verdict
"A strong contender focusing on advanced threat detection through behavioral analysis, suitable for organizations looking beyond signature-based methods."
 #7
#7
Check Point CloudGuard
By Check Point
A unified cloud native security platform providing threat prevention, posture management, workload protection, and network security across multi-cloud environments.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, OCI, VMware, Containers
Best For: CSPM, CWPP, Network Security (Cloud Firewalls), Serverless Security, Application Security
Key Features
- ✓Unified Security Management: Provides a single console for managing various cloud security functions.
- ✓Advanced Threat Prevention: Leverages Check Point's threat intelligence and security technologies.
- ✓Automated Security Posture: Offers CSPM with auto-remediation capabilities.
- ✓Workload & Application Security: Includes protection for VMs, containers, serverless functions, and web applications.
Scorecard (Overall: 7.6 / 10.0)
Pricing
Module-based
Contact Vendor
- Purchase modules like Posture Management, Workload Protection, Network Security
- Available via Cloud Marketplaces
Limitations: Can be complex to choose and price needed modules
Pros
- + Broad portfolio of cloud security tools
- + Strong threat prevention heritage
- + Unified management interface
- + Good automation capabilities
Cons
- - Can feel like multiple products integrated rather than a single seamless platform
- - Interface complexity
- - Agent required for full CWPP
Verdict
"A solid, comprehensive option from a veteran security vendor, offering a wide range of controls but can be complex to manage."
 #6
#6
Zscaler Cloud Protection (ZCP)
By Zscaler
Part of the Zscaler Zero Trust Exchange, ZCP secures cloud workloads and applications, focusing on posture, permissions, and preventing lateral threat movement.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes
Best For: CSPM, CIEM, CWPP, Data Security, Zero Trust Segmentation
Key Features
- ✓Zero Trust Architecture: Applies Zero Trust principles to cloud environments, securing connectivity and access.
- ✓Workload Communications Security: Secures app-to-app and app-to-internet communications without relying on network segmentation.
- ✓Integrated CSPM & CIEM: Identifies misconfigurations and excessive permissions.
- ✓Data Protection: Includes DLP capabilities for cloud environments.
Scorecard (Overall: 7.8 / 10.0)
Pricing
Custom Quote
Contact Vendor
- Based on modules and usage
- Integrated with Zscaler platform
Limitations: Pricing not publicly available, Best utilized within the broader Zscaler ecosystem
Pros
- + Strong Zero Trust approach
- + Effective workload communication security
- + Integrated platform with ZIA/ZPA
- + Good posture and entitlement management
Cons
- - Can be complex to implement
- - Less emphasis on vulnerability scanning compared to some competitors
- - Value maximized when using other Zscaler products
Verdict
"Ideal for organizations committed to a Zero Trust strategy and potentially already using Zscaler, offering strong controls over cloud workload communication and posture."
 #5
#5
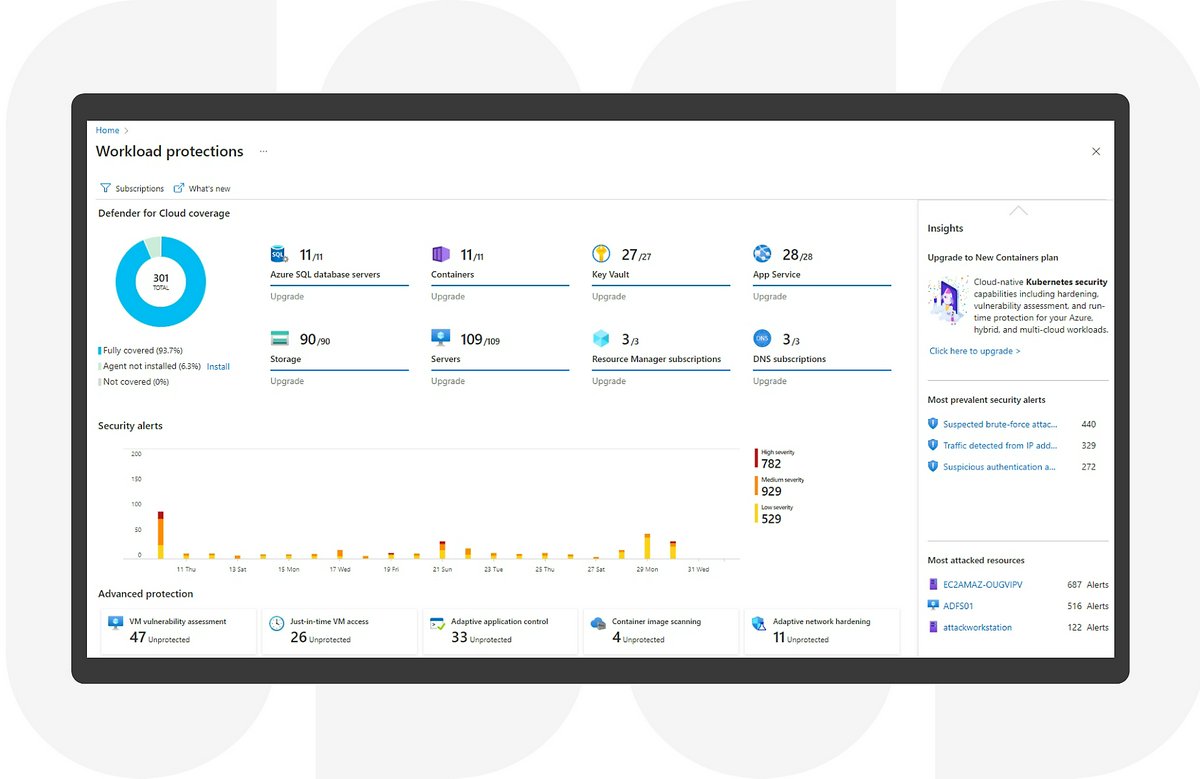
Microsoft Defender for Cloud
By Microsoft
A native cloud security solution offering CSPM and CWPP capabilities, tightly integrated with Azure but also providing multi-cloud support.
Platforms & Use Cases
Platforms: Azure, AWS, GCP, On-premises, Kubernetes
Best For: CSPM, CWPP, Threat Protection, Compliance Management, Security Recommendations
Key Features
- ✓Native Azure Integration: Seamless integration with Azure services and Azure Policy.
- ✓Multi-Cloud Support: Extends protection and posture management to AWS and GCP environments.
- ✓Broad Threat Protection: Covers VMs, databases, containers, storage, App Service, Key Vault, and more.
- ✓Secure Score: Provides recommendations to improve security posture based on industry best practices and compliance standards.
Scorecard (Overall: 8.1 / 10.0)
Pricing
Free Tier (Foundational CSPM)
Contact Vendor
- Continuous assessment
- Secure Score
- Basic recommendations
Defender Plans (Pay-per-resource)
Contact Vendor
- Advanced threat detection
- Vulnerability assessment
- Just-in-time VM access
- Adaptive application controls
- Container security
Limitations: Can become complex to manage pricing across many resource types
Pros
- + Excellent integration with Azure ecosystem
- + Strong CSPM and compliance features
- + Multi-cloud capabilities
- + Competitive pricing, especially for Azure-centric shops
Cons
- - User interface can be complex
- - Multi-cloud features less mature than Azure-native ones
- - Agent deployment required for full CWPP
Verdict
"A compelling choice, particularly for organizations heavily invested in Azure, offering robust native security features and growing multi-cloud support."
 #4
#4
Orca Security
By Orca Security
An agentless cloud security platform providing full-stack visibility and covering vulnerabilities, misconfigurations, malware, identity risks, and data risks.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, Alibaba Cloud, OCI
Best For: CSPM, CWPP (Vulnerability Management), CIEM, DSPM, Container Security, API Security
Key Features
- ✓SideScanning Technology: Patented agentless approach reads workload runtime block storage and cloud configuration APIs.
- ✓Unified Data Model: Contextualizes risks across the cloud estate to prioritize alerts effectively.
- ✓Broad Security Coverage: Scans for vulnerabilities, malware, misconfigurations, identity issues, lateral movement risk, and sensitive data.
- ✓Shift Left Capabilities: Integrates security scanning into CI/CD pipelines.
Scorecard (Overall: 8.2 / 10.0)
Pricing
Custom Quote
Contact Vendor
- Based on the number of assets scanned
- Access to platform features
Limitations: Pricing not publicly available
Pros
- + Deep agentless visibility
- + Fast deployment and broad coverage
- + Effective risk prioritization
- + Easy to use interface
Cons
- - Agentless approach may miss certain real-time runtime events compared to agent-based solutions
- - Newer API security features
Verdict
"A strong agentless competitor to Wiz, offering comprehensive visibility and risk assessment with a focus on ease of deployment and broad coverage."
 #3
#3
Falcon Cloud Security
By CrowdStrike
Extends CrowdStrike's endpoint security leadership to the cloud, focusing on breach protection for cloud workloads, containers, and serverless environments.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, Containers
Best For: CWPP, CSPM, Container Security, Threat Detection & Response
Key Features
- ✓Unified Agent: Leverages the single Falcon agent for both endpoint and cloud workload protection.
- ✓Real-time Threat Detection: Provides runtime protection, threat hunting, and exploit blocking for cloud workloads.
- ✓Managed Threat Hunting: Offers optional expert services (Falcon OverWatch) to hunt for threats in cloud environments.
- ✓Integrated Threat Intelligence: Utilizes CrowdStrike's extensive threat intelligence network.
Scorecard (Overall: 8.3 / 10.0)
Pricing
Module-based
Contact Vendor
- Purchase specific modules (Falcon Cloud Workload Protection, Falcon Horizon CSPM, etc.)
Limitations: Requires Falcon agent deployment for CWPP, CSPM features are newer compared to CWPP
Pros
- + Best-in-class threat detection and response (CWPP)
- + Unified platform with endpoint security
- + Strong threat intelligence integration
- + Managed services option
Cons
- - Agent-based approach for runtime security
- - CSPM capabilities less mature than some competitors
- - Can become costly with multiple modules
Verdict
"Excellent choice for organizations prioritizing runtime threat detection and response for cloud workloads, especially those already using CrowdStrike for endpoint security."
 #2
#2
Wiz
By Wiz
An agentless cloud security platform focusing on deep visibility across multi-cloud environments to identify risks across vulnerabilities, configurations, network, and identity.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, OCI, Alibaba Cloud
Best For: CSPM, CWPP (Vulnerability Management), CIEM, Data Security Posture Management (DSPM), Container Security
Key Features
- ✓Agentless Scanning: Provides full-stack visibility without requiring agents on workloads.
- ✓Security Graph: Correlates risks across different layers (network, identity, secrets, vulnerabilities) to prioritize critical issues.
- ✓Fast Deployment: Connects quickly to cloud environments via APIs for rapid risk assessment.
- ✓Broad Risk Coverage: Identifies misconfigurations, vulnerabilities, exposed secrets, malware, excessive permissions, and network exposure.
Scorecard (Overall: 8.4 / 10.0)
Pricing
Custom Quote
Contact Vendor
- Based on cloud resource consumption
- Access to platform features
Limitations: Pricing not publicly available
Pros
- + Rapid agentless deployment
- + Excellent visibility and risk correlation
- + Intuitive user interface
- + Effective prioritization of risks
Cons
- - Primarily focused on visibility and vulnerability management; less emphasis on runtime protection compared to agent-based CWPPs
- - Can be expensive
Verdict
"Leading agentless solution ideal for organizations prioritizing rapid visibility, risk assessment, and ease of use across complex multi-cloud environments."
View Top Ranked Software
Watch a short ad to unlock the details for the #1 ranked software.
 #1
#1
Prisma Cloud
By Palo Alto Networks
A comprehensive Cloud Native Application Protection Platform (CNAPP) securing applications from code to cloud across multi-cloud environments.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, OCI, Alibaba Cloud, Serverless, Containers
Best For: CSPM, CWPP, CIEM, Code Security, Data Security, Web Application Security, Compliance
Key Features
- ✓Unified Platform: Integrates security across the full application lifecycle (code, build, deploy, run).
- ✓Broad Multi-Cloud Support: Provides consistent security posture management and workload protection across major cloud providers.
- ✓Agent & Agentless Options: Offers flexibility in deployment for workload protection and posture management.
- ✓Identity-Based Microsegmentation: Controls east-west traffic based on workload identity.
Scorecard (Overall: 8.5 / 10.0)
Pricing
Credits-based
Contact Vendor
- Access to various modules based on credit consumption
- Volume discounts
Limitations: Requires careful planning for credit usage
Pros
- + Comprehensive feature set (CNAPP leader)
- + Excellent visibility and context
- + Strong integration capabilities
- + Scalable architecture
Cons
- - Can be complex to configure and manage fully
- - Pricing can be high for smaller organizations
Verdict
"A top-tier, comprehensive CNAPP solution best suited for large enterprises needing extensive multi-cloud security features and deep visibility."

Final Thoughts
The cloud security market offers a range of powerful solutions, from comprehensive CNAPPs like Prisma Cloud to innovative agentless platforms like Wiz and Orca, and specialized runtime protectors like CrowdStrike and Sysdig. Native cloud provider tools like Microsoft Defender for Cloud are increasingly competitive, especially for single-cloud or Azure-centric environments. Selection depends heavily on specific needs: breadth vs. depth, agent vs. agentless preference, primary use cases (CSPM, CWPP, CIEM), and existing security ecosystem.