Top 10 Cloud Security Platforms Comparison
By Lucy Chen | Published: 2025-03-12 | Category: Cloud Security
About Cloud Security
Cloud security encompasses the technologies, policies, controls, and services used to protect cloud-based systems, data, and infrastructure from threats. It aims to ensure data privacy, compliance, and protection against unauthorized access and cyberattacks within cloud environments.
Scoring Criteria
- → Threat Detection & Response
- → Compliance & Governance
- → Configuration Management (CSPM)
- → Workload Protection (CWPP)
- → Integration Capabilities
- → Usability & Reporting
The Best Cloud Security
 #10
#10
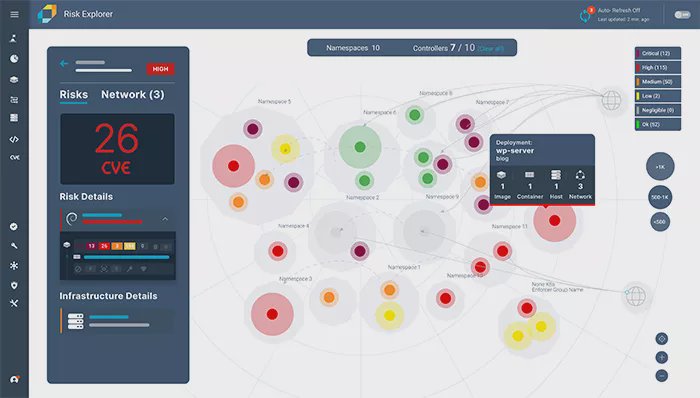
Aqua Cloud Native Security Platform
By Aqua Security
Full lifecycle security platform specializing in protecting container-based, Kubernetes, and serverless applications.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, OpenShift, VMs
Best For: Container Security, Kubernetes Security, CWPP, CSPM, Serverless Security, Shift-Left Security
Key Features
- ✓Image Scanning: Deep vulnerability and malware scanning for container images integrated into CI/CD pipelines.
- ✓Runtime Protection: Policy-based runtime controls for containers, preventing drift and unauthorized activity.
- ✓Kubernetes Security Assurance: Risk assessment, policy enforcement, and security controls specifically for Kubernetes environments.
- ✓Dynamic Threat Analysis (DTA): Analyzes image behavior in a sandbox to detect hidden malware or vulnerabilities.
Scorecard (Overall: 8.6 / 10.0)
Pricing
Team
$-1.00 / Annual
- Basic vulnerability scanning
- CI/CD integration
Limitations: Limited runtime features, Requires vendor quote
Advanced
$-1.00 / Annual
- Full image scanning
- Runtime protection
- Kubernetes assurance
- Compliance
Limitations: Requires vendor quote
Enterprise
$-1.00 / Annual
- Advanced KSPM
- Serverless protection
- VM security
- DTA
Limitations: Requires vendor quote
Pros
- + Market leader in container and Kubernetes security
- + Comprehensive 'shift-left' capabilities
- + Strong runtime protection features
- + Innovative Dynamic Threat Analysis
Cons
- - CSPM features are less comprehensive than market leaders
- - Can be complex to manage all features
- - Primarily focused on cloud-native applications
Verdict
"An excellent choice for organizations heavily utilizing containers and Kubernetes, offering deep security controls throughout the application lifecycle. Strongest in workload protection for cloud-native apps."
 #9
#9
Trend Micro Cloud One
By Trend Micro
A suite of security services designed to protect cloud environments, covering workloads, networks, containers, applications, and file storage.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, VMware, Containers
Best For: CWPP, CSPM, Container Security, File Storage Security, Network Security, Application Security
Key Features
- ✓Workload Security: Comprehensive protection for virtual servers including anti-malware, IPS/IDS, integrity monitoring.
- ✓Container Security: Image scanning in CI/CD pipelines and runtime protection for containers.
- ✓Conformity (CSPM): Cloud security posture management with real-time monitoring and compliance checks.
- ✓Network Security: Cloud network layer IPS/IDS capabilities.
Scorecard (Overall: 8.6 / 10.0)
Pricing
Modular Services
$-1.00 / Annual/Hourly
- Pay for specific services (Workload, Container, Conformity, etc.)
- Multiple billing options (including AWS Marketplace)
Limitations: Pricing varies significantly based on modules and usage, Can be complex to estimate costs
Pros
- + Broad set of security services available
- + Strong traditional workload protection features
- + Flexible modular pricing
- + Good compliance reporting via Conformity
Cons
- - Platform can feel less integrated compared to unified CNAPPs
- - User interface varies across modules
- - Network security features less advanced than dedicated NGFWs
Verdict
"A comprehensive security services platform offering flexibility through its modular approach. Strong contender for organizations looking for specific solutions like robust workload protection or CSPM."
 #8
#8
Sysdig Secure
By Sysdig
Cloud security platform built on open-source Falco, focusing on container, Kubernetes, and cloud threat detection and response.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, OpenShift
Best For: CWPP, Container Security, Kubernetes Security, CSPM, Compliance, Runtime Threat Detection
Key Features
- ✓Runtime Security (Falco): Deep runtime visibility and threat detection based on system calls for containers and hosts.
- ✓Image Scanning: Scans container images for vulnerabilities and misconfigurations throughout the CI/CD pipeline.
- ✓Kubernetes Security Posture Management (KSPM): Assesses Kubernetes configurations against security best practices.
- ✓Compliance Checks: Validates configurations against standards like PCI, NIST, SOC2 for containers and cloud.
Scorecard (Overall: 8.7 / 10.0)
Pricing
Sysdig Secure
$-1.00 / Annual
- Container security
- Cloud security
- Compliance
- Vulnerability management
Limitations: Requires vendor quote, Pricing typically per node/agent
Pros
- + Best-in-class runtime threat detection for containers and Kubernetes
- + Strong open-source foundation (Falco)
- + Excellent visibility into containerized environments
- + Good CI/CD integration
Cons
- - CSPM capabilities are less mature than some competitors
- - User interface can be complex for beginners
- - Primarily focused on container/Kubernetes environments
Verdict
"The top choice for organizations where container and Kubernetes security is paramount. Offers unmatched runtime protection and deep visibility for cloud-native workloads."
 #7
#7
Orca Security
By Orca Security
Agentless cloud security platform using SideScanning technology to provide deep visibility without runtime footprint.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Alibaba Cloud, Kubernetes
Best For: CSPM, CWPP, Vulnerability Management, Compliance, CIEM, Shift-Left Security
Key Features
- ✓SideScanning Technology: Reads workload runtime block storage and cloud configurations out-of-band, eliminating agents.
- ✓Unified Data Model: Contextualizes disparate risks (vulnerabilities, misconfigurations, malware, lateral movement risk, sensitive data) in one platform.
- ✓Full Cloud Coverage: Scans VMs, containers, serverless functions, and cloud configuration.
- ✓Compliance Frameworks: Built-in support for numerous compliance standards and automated checks.
Scorecard (Overall: 8.7 / 10.0)
Pricing
Platform Subscription
$-1.00 / Annual
- Full platform access
- Pricing based on number of assets scanned
Limitations: Requires vendor quote
Pros
- + Agentless deployment simplifies operations
- + Deep visibility into workloads without performance impact
- + Unified view of various risks
- + Easy to deploy and manage
Cons
- - SideScanning provides point-in-time snapshots, not real-time runtime protection like agents
- - Threat response capabilities are less developed than some competitors
Verdict
"A leading agentless platform offering comprehensive visibility and risk assessment with minimal operational overhead. Excellent for organizations prioritizing ease of deployment and broad scanning."
 #6
#6
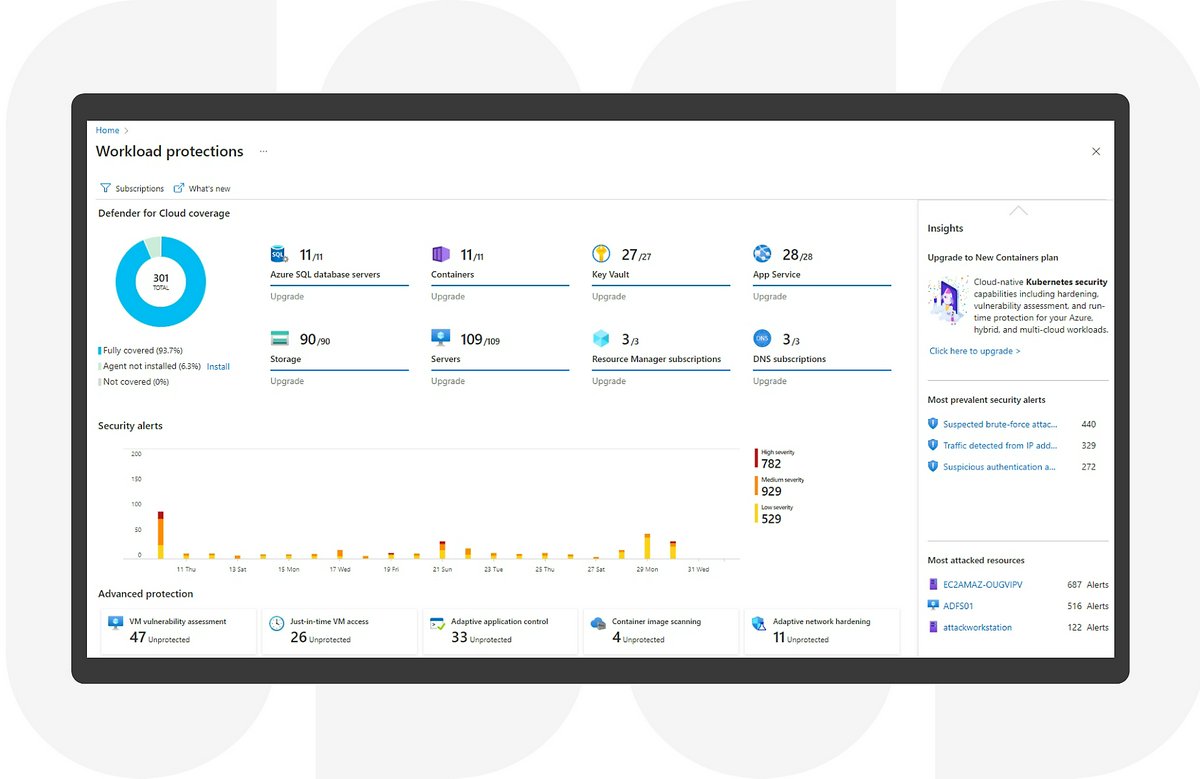
Microsoft Defender for Cloud
By Microsoft
Native Azure security solution providing CSPM and CWPP capabilities, with extensions for multi-cloud environments.
Platforms & Use Cases
Platforms: Azure, AWS, GCP, On-premises
Best For: CSPM, CWPP, Security Recommendations, Regulatory Compliance, Threat Protection
Key Features
- ✓Secure Score: Provides a prioritized view of security recommendations for Azure resources.
- ✓Regulatory Compliance Dashboard: Tracks compliance status against various standards.
- ✓Enhanced Security Features: Includes threat protection for various Azure services (VMs, Storage, SQL, Containers, etc.).
- ✓Multi-cloud Support: Connectors for AWS and GCP provide CSPM and limited CWPP capabilities outside Azure.
Scorecard (Overall: 8.8 / 10.0)
Pricing
Free Tier
Contact Vendor
- Continuous assessment
- Secure Score
- Basic recommendations
Limitations: Limited threat protection
Enhanced Security (Defender Plans)
$-1.00 / Monthly
- Full threat protection for selected services
- Vulnerability Assessment
- JIT VM access
- Adaptive Application Controls
Limitations: Priced per protected resource/service, Can become costly
Pros
- + Deep integration with Azure services
- + Strong CSPM capabilities within Azure
- + Good compliance features
- + Simplified deployment for Azure environments
Cons
- - Multi-cloud capabilities less comprehensive than Azure-native features
- - CWPP features lag behind some specialized competitors, especially outside Azure
Verdict
"The default choice for organizations heavily invested in Azure. Offers excellent integration and strong CSPM, with improving multi-cloud support."
 #5
#5
Lacework Platform
By Lacework
Data-driven cloud security platform using anomaly detection to identify threats and misconfigurations across multi-cloud environments.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes
Best For: CNAPP, CSPM, CWPP, Container Security, Compliance, Anomaly Detection
Key Features
- ✓Polygraph Data Platform: Builds behavioral baselines to detect anomalies in cloud activities and workloads.
- ✓Continuous Configuration Monitoring: Identifies misconfigurations and compliance violations in real-time.
- ✓Workload & Container Security: Vulnerability scanning and runtime threat detection for VMs, containers, and hosts.
- ✓Automated Investigation: Provides context and correlation for security events to speed up investigation.
Scorecard (Overall: 8.7 / 10.0)
Pricing
Usage-Based
$-1.00 / Annual
- Full platform access
- Pricing based on monitored resources (VMs, containers, accounts)
Limitations: Requires vendor quote
Pros
- + Strong anomaly detection capabilities
- + Good visualization of cloud activities
- + Unified platform for multiple security functions
- + Effective container security features
Cons
- - Anomaly detection can sometimes lead to false positives initially
- - Requires some tuning to optimize baseline behaviors
Verdict
"A powerful platform leveraging behavioral anomaly detection for threat identification. Particularly effective for dynamic cloud environments where known signatures might fall short."
 #4
#4
CrowdStrike Falcon Cloud Security
By CrowdStrike
Integrated platform extending CrowdStrike's endpoint security leadership into cloud security, focusing on breach prevention.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Containers
Best For: CSPM, CWPP, Container Security, Threat Detection & Response
Key Features
- ✓Unified Agent (Falcon Sensor): Single lightweight agent for both endpoint and cloud workload protection.
- ✓Threat Graph: Correlates security telemetry across endpoints, cloud workloads, and identity for faster detection.
- ✓Real-time Visibility: Continuous monitoring of cloud assets, configurations, and threats.
- ✓Managed Threat Hunting: Optional service providing expert monitoring and threat hunting (Falcon OverWatch).
Scorecard (Overall: 8.9 / 10.0)
Pricing
Falcon Cloud Security Modules
$-1.00 / Annual
- Modular pricing based on required capabilities (Discover, Prevent, Horizon)
- Per-node or per-resource pricing
Limitations: Requires vendor quote, Can become expensive as modules are added
Pros
- + Industry-leading threat detection and response capabilities
- + Unified agent simplifies deployment on workloads
- + Strong integration with endpoint security
- + Excellent managed services options
Cons
- - CSPM features are less mature than some dedicated competitors
- - Focus is heavily skewed towards threat detection and workload protection
Verdict
"An excellent choice for organizations prioritizing best-in-class threat detection and response, particularly those already invested in CrowdStrike's endpoint platform. Strongest in CWPP."
 #3
#3
Wiz
By Wiz
Agentless CNAPP platform focused on providing full stack visibility and risk prioritization across cloud environments.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, OCI, Kubernetes
Best For: CNAPP, CSPM, CWPP, Vulnerability Management, CIEM, Container Security
Key Features
- ✓Agentless Scanning: Scans cloud environments without requiring agents on workloads, simplifying deployment.
- ✓Security Graph: Visualizes toxic combinations of risks across network exposure, vulnerabilities, secrets, and permissions.
- ✓Risk Prioritization: Focuses on identifying and prioritizing the most critical risks based on potential impact.
- ✓Broad Coverage: Covers IaaS, PaaS, containers, serverless, and data stores.
Scorecard (Overall: 8.9 / 10.0)
Pricing
Platform Access
$-1.00 / Annual
- Full platform capabilities
- Usage-based pricing
Limitations: Requires vendor quote, High volume pricing model best suited for larger organizations
Pros
- + Excellent visualization and risk prioritization (Security Graph)
- + Rapid, agentless deployment
- + Intuitive user interface
- + Comprehensive asset visibility
Cons
- - Agentless approach may have limitations for deep runtime protection compared to agent-based CWPP
- - Premium pricing
Verdict
"A highly innovative and user-friendly CNAPP, excelling in risk visualization and prioritization through its agentless approach. Ideal for organizations prioritizing ease of deployment and contextual risk assessment."
 #2
#2
CloudGuard
By Check Point
Unified cloud native security platform providing posture management, workload protection, network security, and application security.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, Kubernetes, VMware
Best For: CSPM, CWPP, Cloud Network Security, Serverless Security, AppSec
Key Features
- ✓Posture Management: Automated discovery and assessment of cloud security posture against best practices and compliance frameworks.
- ✓Workload Protection: Runtime protection for VMs, containers, and serverless functions against vulnerabilities and malware.
- ✓Intelligence and Threat Hunting: Leverages Check Point ThreatCloud for real-time threat intelligence feeds and proactive hunting.
- ✓Unified Management: Centralized console for managing diverse cloud security functions.
Scorecard (Overall: 8.9 / 10.0)
Pricing
Pro
$-1.00 / Annual
- CSPM
- Basic CWPP
- Compliance Reporting
Limitations: Requires vendor quote
Enterprise
$-1.00 / Annual
- Advanced CWPP
- Serverless Protection
- Threat Hunting
- Full API Access
Limitations: Requires vendor quote
Pros
- + Strong threat intelligence integration
- + Comprehensive workload protection capabilities
- + Unified policy management
- + Good support for hybrid environments
Cons
- - Interface can feel slightly dated compared to some competitors
- - Pricing details require direct engagement
Verdict
"A robust and well-integrated cloud security platform from a veteran security vendor, offering strong protection especially for workloads and network security."
View Top Ranked Software
Watch a short ad to unlock the details for the #1 ranked software.
 #1
#1
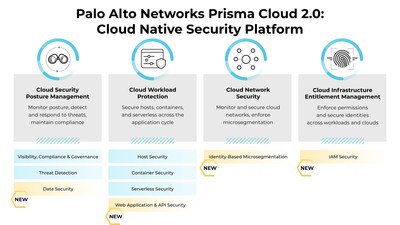
GuardianCloud Suite
By Palo Alto Networks (Prisma Cloud)
Comprehensive Cloud Native Application Protection Platform (CNAPP) offering broad security coverage across the application lifecycle.
Platforms & Use Cases
Platforms: AWS, Azure, GCP, OCI, Alibaba Cloud, Kubernetes
Best For: CNAPP, CSPM, CWPP, Cloud Code Security, CIEM
Key Features
- ✓Unified Visibility: Single pane of glass for multi-cloud asset inventory, configuration, and security posture.
- ✓Full Lifecycle Security: Scans code, secures infrastructure, protects runtime workloads, and manages entitlements.
- ✓Advanced Threat Detection: Utilizes machine learning and threat intelligence for detecting misconfigurations, vulnerabilities, and active threats.
- ✓Compliance Monitoring: Continuous monitoring and reporting against various industry standards (PCI DSS, HIPAA, SOC 2, etc.).
Scorecard (Overall: 9.2 / 10.0)
Pricing
Credits-based
$-1.00 / Annual
- Full platform access
- Pay-as-you-go consumption model based on resource units
Limitations: Pricing requires vendor quote and depends heavily on usage.
Pros
- + Extremely comprehensive feature set
- + Strong multi-cloud and Kubernetes support
- + Excellent threat intelligence integration
- + Covers entire application lifecycle
Cons
- - Can be complex to configure initially
- - Pricing model can be difficult to predict
Verdict
"A market-leading CNAPP solution offering unparalleled depth and breadth of cloud security capabilities, ideal for large enterprises with complex multi-cloud environments."

Final Thoughts
The cloud security market is rapidly evolving, with leading platforms consolidating capabilities into comprehensive CNAPPs. Key differentiators include the breadth of coverage (multi-cloud, containers, serverless), the depth of protection (CSPM, CWPP, CIEM), deployment models (agent vs. agentless), and usability. While top-tier solutions offer extensive features, evaluating specific use cases and integration needs remains crucial.