Top 10 DevOps Security Platforms Reviewed
By Jordan Patel | Published: 2025-03-19 | Category: Devops Security
About Devops Security
DevOps Security, often termed DevSecOps, integrates security practices and tools seamlessly into the DevOps lifecycle, from development to deployment and operations. The goal is to automate security checks and embed security thinking throughout the software development process.
How We Evaluated
Providers were evaluated based on their range of security capabilities across the SDLC, developer-friendliness, integration options, enterprise features, and overall market perception. Scoring reflects a composite assessment across these dimensions.
Rating Criteria
- → Coverage Breadth
- → Developer Experience
- → Accuracy & Reliability
- → Enterprise Scalability
- → Pricing & Value
The Best Devops Security
SonarSource
Visit Website →Specializes in code quality and code security, offering static analysis tools (SonarQube, SonarLint, SonarCloud) to detect bugs and vulnerabilities.
Target Audience
Developers, Quality Assurance, Security Teams, SMB, Enterprise
Service Offerings
SonarQube
Self-hosted static code analysis platform for continuous code quality and security.
- SAST
- Security hotspots review
- Code quality metrics
- Broad language support
SonarCloud
Cloud-based version of SonarQube, integrated with cloud DevOps platforms.
- SAST
- Integration with GitHub, GitLab, Bitbucket, Azure DevOps
SonarLint
IDE extension providing real-time feedback on code quality and security issues.
- On-the-fly detection
- Connects to SonarQube/SonarCloud
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Free Tier (Community Edition/SonarCloud Free)
Basic code quality and security for open source projects.
Developer/Commercial Editions
Tiered pricing based on lines of code or users, adding more security features and languages.
Pros
- + Market leader in code quality and static analysis (SAST)
- + Excellent developer integration (SonarLint)
- + High accuracy and low false positive rates
- + Strong community and language support
Cons
- - Primarily focused on static code analysis (SAST)
- - Lacks broader DevSecOps capabilities like DAST, SCA, Container Scanning
- - Security features gated behind paid tiers
Verdict
"SonarSource provides best-in-class static code analysis for improving code quality and finding security vulnerabilities early, with excellent developer tooling."
Rapid7
Visit Website →Provides security analytics and automation solutions, including application security testing (DAST) and cloud security posture management.
Target Audience
Security Teams, Operations, Enterprise
Service Offerings
InsightAppSec
Dynamic Application Security Testing (DAST) solution.
- Cloud and on-premise scanning
- Attack replay
- CI/CD integration
InsightCloudSec
Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWPP).
- Multi-cloud support
- Compliance monitoring
- Kubernetes security
- IaC scanning
InsightVM
Vulnerability management for infrastructure.
- Network scanning
- Risk prioritization
Scorecard (Overall: 7.2 / 10.0)
Pricing Model
Subscription
Typically based on number of apps, cloud resources, or assets scanned.
Pros
- + Mature DAST and vulnerability management capabilities
- + Strong cloud security posture management
- + Integrated platform approach (Insight)
- + Good reporting and analytics
Cons
- - Less focus on SAST and SCA compared to others
- - Developer experience can be less intuitive
- - Platform integration sometimes feels disjointed
Verdict
"Rapid7 offers strong DAST and cloud security solutions, particularly suited for security teams needing robust vulnerability assessment and posture management."
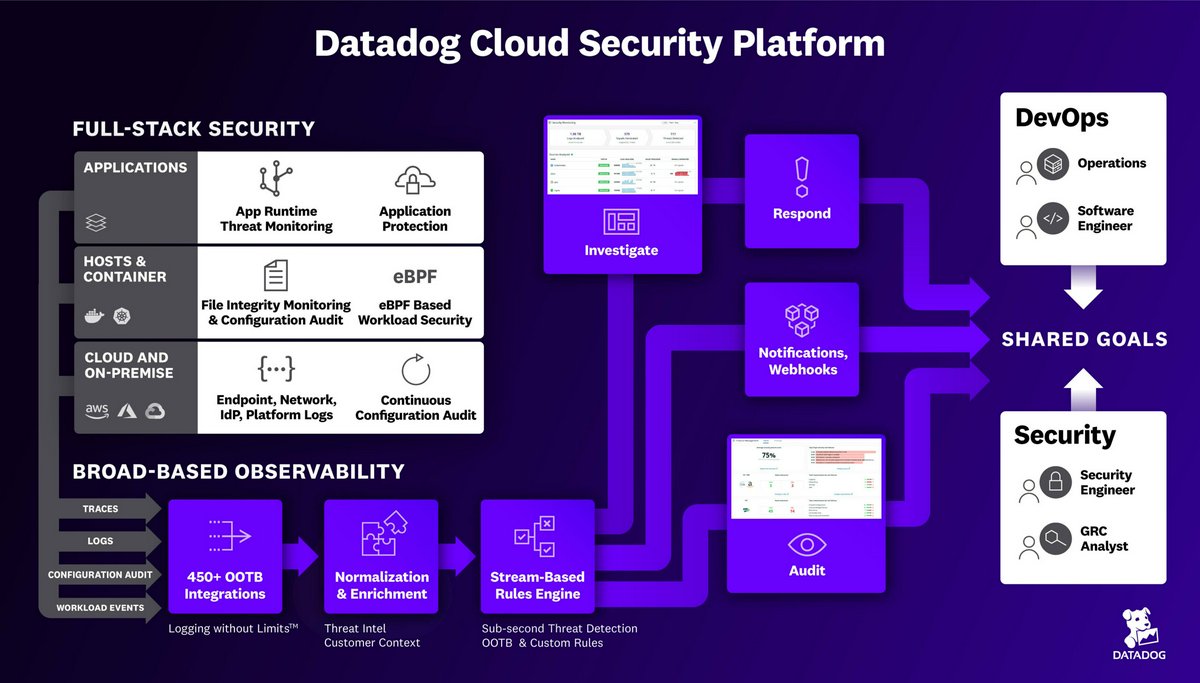
Datadog
Visit Website →A monitoring and analytics platform that includes security monitoring capabilities for cloud applications, infrastructure, and logs.
Target Audience
DevOps Teams, Security Teams, Operations, Developers
Service Offerings
Cloud Security Posture Management (CSPM)
Scans cloud environments for misconfigurations and compliance violations.
- Configuration checks
- Compliance reporting
Cloud Workload Security (CWS)
Real-time threat detection for hosts and containers.
- File integrity monitoring
- Workload behavior analysis
Application Security Management (ASM)
Detects and blocks threats targeting applications in production.
- In-app WAF
- Code-level vulnerability detection (IAST-like)
- Attack tracing
Sensitive Data Scanner
Scans logs and events for sensitive data patterns.
- PII detection
- Compliance aid
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Modular Subscription
Per-host, per-scan, or per-GB pricing depending on the module.
Pros
- + Unified platform for observability and security
- + Strong integration with monitoring data
- + Real-time threat detection capabilities
- + Good user experience
Cons
- - Security features are newer compared to specialized vendors
- - Less focus on pre-deployment scanning (SAST/SCA)
- - Can get expensive with multiple modules
Verdict
"Datadog excels at integrating security monitoring into its observability platform, offering strong runtime detection and posture management for teams already invested in its ecosystem."
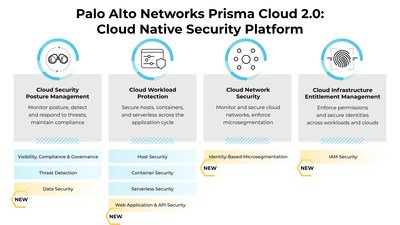
Palo Alto Networks (Prisma Cloud)
Visit Website →Prisma Cloud provides a comprehensive Cloud Native Application Protection Platform (CNAPP) securing applications from code to cloud.
Target Audience
Security Teams, Cloud Architects, DevOps Teams, Enterprise
Service Offerings
Cloud Security Posture Management (CSPM)
Multi-cloud visibility, compliance monitoring, and threat detection.
- Configuration assessment
- Compliance reporting
Cloud Workload Protection Platform (CWPP)
Secures hosts, containers, and serverless functions across the lifecycle.
- Vulnerability scanning
- Runtime defense
- WAAS
Cloud Network Security
Microsegmentation and network visibility for cloud environments.
- Network flow analysis
- Firewall policies
Cloud Infrastructure Entitlement Management (CIEM)
Manages cloud identities and entitlements.
- Least privilege analysis
- Permission governance
Application Security (Twistlock & PureSec lineage)
Integrated scanning (IaC, SCA, Container) and protection.
- CI/CD integration
- Serverless security
- API security
Scorecard (Overall: 8.4 / 10.0)
Pricing Model
Credit-based Subscription
Flexible licensing based on resource consumption across modules.
Pros
- + Extremely comprehensive CNAPP platform
- + Strong integration across security domains (CSPM, CWPP, CIEM, Network)
- + Leverages strong threat intelligence
- + Excellent scalability for large enterprises
Cons
- - Can be very complex and overwhelming
- - Higher price point
- - Shift-left/developer tooling less emphasized than cloud posture/runtime
Verdict
"Prisma Cloud offers one of the most comprehensive cloud-native security platforms available, ideal for large organizations needing integrated security across their entire cloud footprint."
Aqua Security
Visit Website →A cloud-native security platform focused on securing containerized applications, Kubernetes environments, and serverless functions from development to production.
Target Audience
Security Teams, DevOps Teams, Cloud Architects, Enterprise
Service Offerings
Image Scanning
Vulnerability and malware scanning for container images.
- CI/CD integration
- Registry scanning
- Risk assessment
Runtime Protection
Container runtime security, drift prevention, and threat detection.
- Behavioral analysis
- Policy enforcement
- Forensics
Kubernetes Security Posture Management (KSPM)
Risk assessment and compliance for Kubernetes clusters.
- CIS benchmarks
- RBAC analysis
Dynamic Threat Analysis (DTA)
Analyzes container image behavior in a sandbox before deployment.
- Detects hidden malware
- Zero-day threat detection
Serverless Security
Security scanning and runtime protection for serverless functions.
- Vulnerability management
- Permission checks
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Subscription
Custom pricing based on nodes, functions, or platform usage.
Pros
- + Leader in cloud-native and container security
- + Comprehensive protection from build to runtime
- + Strong Kubernetes security features
- + Advanced threat detection capabilities
Cons
- - Primarily focused on cloud-native environments
- - Can be complex to deploy and manage
- - Developer-facing tools less prominent than runtime features
Verdict
"Aqua Security is a top choice for securing containerized and cloud-native applications throughout their lifecycle, offering deep visibility and runtime protection."
JFrog
Visit Website →Provides the JFrog Platform including Artifactory for artifact management and Xray for continuous security and compliance scanning of binaries and dependencies.
Target Audience
DevOps Teams, Security Teams, Developers, Enterprise
Service Offerings
JFrog Xray
Security and compliance analysis integrated with Artifactory.
- Deep binary scanning (SCA)
- License compliance
- Operational risk assessment
- IDE integration
- CI/CD integration
JFrog Artifactory
Universal artifact repository manager.
- Centralized binary management
- Supports multiple package types
Scorecard (Overall: 7.8 / 10.0)
Pricing Model
Free Tier (Cloud)
Limited storage and transfer.
Pro/Enterprise Tiers
Tiered pricing based on features, storage, data transfer (Cloud) or server count (Self-Hosted). Xray often bundled or add-on.
Pros
- + Deep integration with artifact management (Artifactory)
- + Strong binary analysis capabilities (SCA)
- + Good enterprise scalability and support
- + Focus on securing the software supply chain
Cons
- - Primarily focused on SCA and artifact security, less on SAST/DAST
- - Can be complex to set up and configure
- - Value depends heavily on using the full JFrog platform
Verdict
"JFrog Xray excels at securing the software supply chain through deep binary analysis and tight integration with Artifactory, ideal for organizations prioritizing artifact security."
GitLab
Visit Website →A complete DevOps platform with integrated security scanning features (SAST, DAST, SCA, Secret Detection, etc.) within its CI/CD pipelines.
Target Audience
Developers, DevOps Teams, Security Teams, SMB, Enterprise
Service Offerings
SAST
Static Application Security Testing integrated into CI pipelines.
- Multiple language support
- Vulnerability management within MRs
DAST
Dynamic Application Security Testing for web applications.
- Runs against review apps or live environments
Dependency Scanning
Software Composition Analysis integrated into pipelines.
- Detects vulnerable libraries
Secret Detection
Scans repository history and CI jobs for leaked secrets.
- Prevents accidental commits
Container Scanning
Scans container images for known vulnerabilities.
- Integrates with registry
Scorecard (Overall: 8.2 / 10.0)
Pricing Model
Free Tier
Basic DevOps features, limited security scans.
Premium Tier
Enhanced CI/CD, basic security features.
Ultimate Tier
Full DevSecOps capabilities, advanced security testing, compliance.
Pros
- + Fully integrated DevOps and Security platform
- + Excellent developer workflow integration
- + Single application simplifies toolchain
- + Good value, especially if already using GitLab CI/CD
Cons
- - Security features primarily tied to Ultimate tier
- - Scan accuracy/depth may lag behind specialized tools for some technologies
- - Can be complex to manage all features
Verdict
"GitLab provides exceptional value and integration for teams seeking a unified DevOps platform with built-in security scanning capabilities."
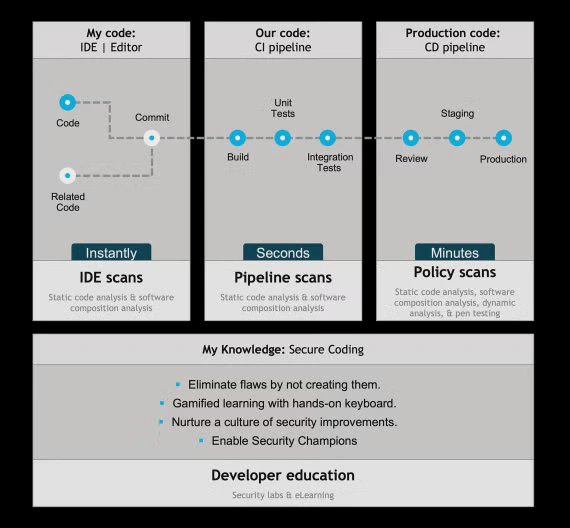
Veracode
Visit Website →A cloud-native application security platform offering SAST, DAST, SCA, and developer training, focused on integrating security into the SDLC.
Target Audience
Security Teams, Developers, Enterprise, Regulated Industries
Service Offerings
Static Analysis
Cloud-based SAST engine for identifying flaws in code.
- Binary analysis capability
- Policy management
- IDE & CI/CD integration
Dynamic Analysis (DAST)
Scans running web applications for vulnerabilities.
- Automated crawling
- Authentication support
Software Composition Analysis (SCA)
Analyzes open source components for vulnerabilities and license risks.
- Dependency tracking
- Policy enforcement
Developer Enablement
Tools and training including IDE scans, security labs, and remediation guidance.
- Contextual learning
- Fix suggestions
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Platform Subscription
Custom pricing based on applications, scan types, and usage.
Pros
- + Comprehensive platform with SAST, DAST, and SCA
- + Strong policy and compliance features
- + Mature cloud platform requires less infrastructure management
- + Developer training resources
Cons
- - Scan times can sometimes be long
- - Developer experience not always as seamless as competitors
- - Can be expensive
Verdict
"Veracode offers a robust, policy-driven application security platform well-suited for enterprises needing broad coverage and compliance capabilities."
Checkmarx
Visit Website →Provides a comprehensive software security platform covering SAST, SCA, IaC scanning, and API security, suitable for large enterprises.
Target Audience
Security Teams, Developers, Enterprise
Service Offerings
Checkmarx SAST
Static Application Security Testing tool known for broad language support and accuracy.
- Incremental scanning
- Detailed vulnerability reporting
- CI/CD integration
Checkmarx SCA
Software Composition Analysis identifying vulnerabilities and licenses in open source components.
- Dependency graph analysis
- Policy enforcement
Checkmarx IaC Security (KICS)
Open-source solution for finding security vulnerabilities, compliance issues, and misconfigurations in IaC.
- Wide platform support
- Community driven
Checkmarx API Security
Detects vulnerabilities and threats in APIs throughout the development lifecycle.
- Shadow API discovery
- Runtime protection integration
Scorecard (Overall: 8.2 / 10.0)
Pricing Model
Subscription
Typically custom enterprise agreements based on application count or developers.
Pros
- + Mature and highly accurate SAST engine
- + Comprehensive platform offering
- + Strong enterprise features and support
- + KICS provides robust IaC scanning
Cons
- - Can be complex to manage and configure
- - Developer experience lags behind some newer tools
- - Higher cost
Verdict
"Checkmarx is a powerful, enterprise-grade DevSecOps platform offering deep security analysis, particularly strong in SAST accuracy and compliance."
View Top Ranked Provider
Watch a short ad to unlock the details for the #1 ranked provider.
Snyk
Visit Website →A developer-focused security platform for finding and fixing vulnerabilities in code, open source dependencies, containers, and infrastructure as code.
Target Audience
Developers, Security Teams, SMB, Enterprise
Service Offerings
Snyk Code
Static Application Security Testing (SAST) focused on developer workflow.
- Real-time code analysis
- IDE integration
- AI-powered fixes
Snyk Open Source
Software Composition Analysis (SCA) to manage open source vulnerabilities and licenses.
- Dependency scanning
- License compliance
- Automated remediation paths
Snyk Container
Container image scanning for vulnerabilities.
- Base image analysis
- Workload scanning
- Prioritization
Snyk Infrastructure as Code (IaC)
Security scanning for IaC configuration files.
- Terraform, CloudFormation, Kubernetes support
- Misconfiguration detection
Scorecard (Overall: 8.4 / 10.0)
Pricing Model
Free Tier
Limited usage for individual developers.
Team Tier
Per developer pricing for smaller teams.
Business/Enterprise Tier
Custom pricing based on usage and features.
Pros
- + Excellent developer experience and integration
- + Strong focus on actionable remediation
- + Comprehensive SCA capabilities
- + Free tier available
Cons
- - Advanced reporting can be limited compared to some enterprise tools
- - Can become expensive at scale
Verdict
"Snyk excels with its developer-first approach, seamlessly integrating security into existing workflows, particularly strong in open source and code analysis."

Final Recommendation
The DevOps Security landscape offers diverse solutions, ranging from developer-centric tools like Snyk and SonarSource to comprehensive enterprise platforms like Checkmarx, Veracode, and Prisma Cloud. Integrated DevOps platforms like GitLab provide compelling value, while specialists like Aqua Security dominate cloud-native security. The best choice depends on specific needs regarding coverage breadth, developer integration, runtime protection, and existing toolchains.