Top 10 Cloud Security Governance Solutions
By Sheila Morgan | Published: 2025-03-05 | Category: Cloud Security Governance
About Cloud Security Governance
Cloud Security Governance involves defining and enforcing policies to manage risk, ensure compliance, and maintain security posture across cloud environments. It encompasses identity management, data protection, configuration management, and compliance monitoring within cloud services.
How We Evaluated
Providers were evaluated based on their platform's core governance capabilities, multi-cloud support, automation features, integration potential, compliance management strength, and overall market presence. Scores reflect a consolidated view of features and industry perception.
Rating Criteria
- → Policy & Compliance Management
- → Visibility & Monitoring
- → Automation & Remediation
- → Multi-Cloud Support
- → Integration Capabilities
- → Threat Detection Linkage
The Best Cloud Security Governance
Google Cloud Platform (GCP)
Visit Website →Offers native security and governance tools within GCP, emphasizing data security, policy enforcement, and integrated security analytics.
Target Audience
Organizations using GCP, Data-centric businesses, Google ecosystem users
Service Offerings
Google Cloud Security Command Center (SCC)
Provides centralized visibility and control over security posture, including asset discovery, vulnerability detection, and compliance monitoring.
- Security posture dashboard
- Threat detection (integrates Event Threat Detection, etc.)
- Compliance reporting
- Asset inventory
Organization Policy Service
Allows centralized, programmatic control over organization's cloud resources to enforce constraints.
- Policy constraints (e.g., restrict resource locations)
- Hierarchical policy enforcement
IAM Recommender
Uses machine learning to provide recommendations for removing excessive permissions.
- Least privilege enforcement
- Role recommendations
Scorecard (Overall: 7.2 / 10.0)
Pricing Model
Usage-based
SCC has Standard and Premium tiers. Standard is free; Premium pricing is based on usage (e.g., resources scanned, findings). Other services priced based on consumption. Check GCP pricing.
Pros
- + Strong integration with GCP services
- + Leverages Google's strengths in data analytics and AI/ML
- + Good tools for identity and policy management
- + Scalable infrastructure
Cons
- - Historically weaker multi-cloud story compared to third parties (though improving)
- - Can be complex to navigate the different security services
- - Feature set sometimes lags Azure/AWS native tools
Verdict
"The primary choice for governance within GCP, offering powerful native tools, particularly around data security and identity, but often requires supplementary tools for true multi-cloud management."
Amazon Web Services (AWS)
Visit Website →Offers a suite of native services for security governance within the AWS cloud, focusing on configuration, compliance, and security posture.
Target Audience
Organizations primarily using AWS, Businesses of all sizes on AWS
Service Offerings
AWS Security Hub
Provides a comprehensive view of high-priority security alerts and compliance status across AWS accounts.
- Aggregated findings from various AWS services
- Automated compliance checks (CIS, PCI DSS)
- Security best practice recommendations
AWS Config
Enables assessment, auditing, and evaluation of the configurations of AWS resources.
- Resource configuration tracking
- Compliance auditing using Config Rules
- Configuration change history
AWS Control Tower
Helps set up and govern a secure, multi-account AWS environment based on best practices.
- Automated landing zone setup
- Guardrails (preventive and detective controls)
- Account Factory
AWS Identity and Access Management (IAM)
Manages access to AWS services and resources securely.
- Fine-grained access control
- IAM Access Analyzer
- Role-based access
Scorecard (Overall: 7.5 / 10.0)
Pricing Model
Usage-based
Pricing varies by service. Security Hub, Config, and others often have free tiers followed by charges based on usage (e.g., number of checks, configuration items recorded). See AWS pricing.
Pros
- + Deepest integration with AWS services
- + Often cost-effective for AWS-centric organizations
- + Continuously evolving feature set
- + Leverages AWS scale and reliability
Cons
- - Primarily focused on AWS ecosystem, limited native multi-cloud governance
- - Can require expertise to configure and manage effectively across services
Verdict
"The essential choice for robust security governance within AWS environments, offering unparalleled integration but requiring third-party tools for comprehensive multi-cloud oversight."
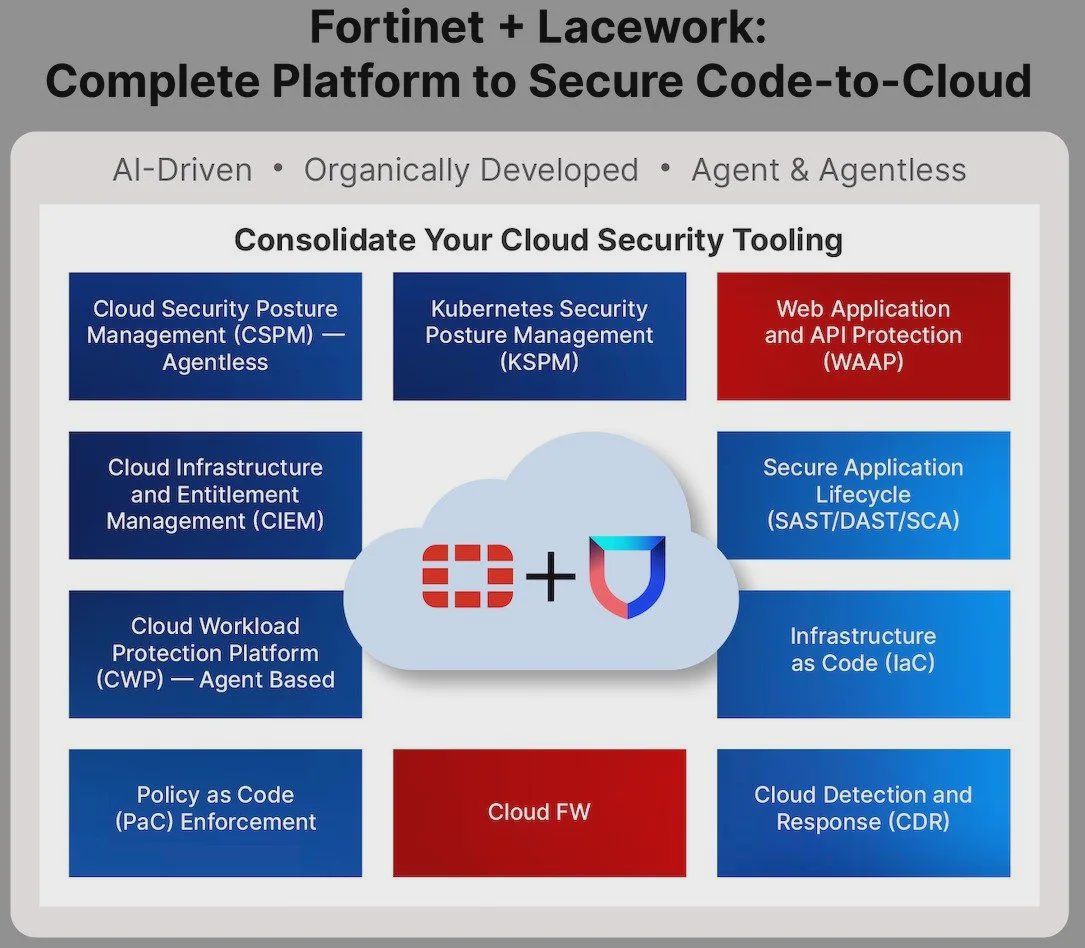
Fortinet
Visit Website →Provides cloud security solutions as part of its broad Security Fabric, offering integrated posture management, threat protection, and network security.
Target Audience
Enterprises, Mid-Market, Existing Fortinet customers
Service Offerings
FortiCWP (Cloud Workload Protection)
Offers CSPM features including configuration monitoring, compliance reporting, and data security across multi-cloud environments.
- Misconfiguration detection
- Compliance monitoring
- Threat detection based on user behavior
- Data Loss Prevention (DLP) integration
FortiCASB (Cloud Access Security Broker)
Provides visibility and control over SaaS applications, often integrated with broader cloud governance.
- SaaS application discovery
- Data security policies
- Threat protection
Fortinet Security Fabric
The overarching architecture integrating various Fortinet products for broader visibility and control.
- Centralized Management
- Automated Workflows
- Threat Intelligence Sharing
Scorecard (Overall: 7.5 / 10.0)
Pricing Model
Custom
Pricing typically depends on the specific products, number of protected resources or users, and subscription term. Contact sales.
Pros
- + Integration with the extensive Fortinet Security Fabric
- + Broad portfolio covering network, endpoint, and cloud
- + Good multi-cloud support
- + Centralized management potential
Cons
- - CSPM features might be less deep than specialized vendors
- - Can feel like a network security vendor extending into cloud
- - Interface complexity
Verdict
"A suitable option for organizations already utilizing the Fortinet Security Fabric, seeking to extend consistent security policies and management into their cloud environments."
CrowdStrike
Visit Website →Primarily known for endpoint and workload security, CrowdStrike Falcon Cloud Security extends its capabilities to cloud posture management and governance.
Target Audience
Enterprises, Organizations prioritizing threat detection, CrowdStrike customers
Service Offerings
Falcon Cloud Security Posture Management (CSPM)
Provides visibility into multi-cloud environments, detects misconfigurations, and monitors compliance.
- Continuous monitoring (AWS, Azure, GCP)
- Compliance reporting
- Guided remediation steps
- Integration with Falcon platform
Falcon Cloud Workload Protection (CWP)
Secures cloud workloads, linking runtime threats back to posture weaknesses.
- Runtime protection
- Vulnerability management
- Threat detection
Scorecard (Overall: 7.8 / 10.0)
Pricing Model
Custom
Pricing based on modules selected and the number of nodes or cloud resources. Contact sales.
Pros
- + Exceptional threat detection and response integration
- + Unified agent for endpoint and cloud workloads
- + Strong visibility into workload security
- + Growing CSPM capabilities
Cons
- - CSPM features may be less mature than dedicated specialists
- - More focused on threat detection than broad policy governance
Verdict
"A top choice for organizations prioritizing the linkage between cloud posture and active threat detection, leveraging CrowdStrike's leading EDR/XDR capabilities."
Check Point Software Technologies
Visit Website →A long-standing cybersecurity vendor offering the CloudGuard platform for unified cloud security, including posture management and governance.
Target Audience
Enterprises, Mid-Market, Existing Check Point customers
Service Offerings
CloudGuard Posture Management
Delivers CSPM capabilities across multi-cloud platforms, focusing on compliance and security configuration.
- Compliance Engine (CIS, NIST, PCI DSS, HIPAA)
- Misconfiguration Detection
- Visualization of Cloud Assets
- Automated Remediation options
CloudGuard Workload Protection
Provides security for cloud-native workloads, including serverless and containers.
- Runtime Protection
- Vulnerability Scanning
- Admission Control
CloudGuard Network Security
Offers advanced threat prevention and automated cloud network security.
- Cloud Firewall
- Intrusion Prevention
- Data Loss Prevention
Scorecard (Overall: 7.8 / 10.0)
Pricing Model
Custom
Pricing depends on the specific CloudGuard products and the scale of deployment (e.g., number of assets). Contact sales.
Pros
- + Unified platform for various cloud security needs
- + Strong threat prevention heritage
- + Good multi-cloud support
- + Integrates with broader Check Point ecosystem
Cons
- - Interface can sometimes feel less modern than cloud-native competitors
- - Licensing across modules can be complex
Verdict
"A solid, comprehensive option from an established security vendor, particularly suitable for organizations already invested in the Check Point ecosystem or seeking a unified security console."
Zscaler
Visit Website →A leader in cloud-native security, offering Zero Trust solutions that include robust cloud security posture management and workload protection.
Target Audience
Enterprises, Organizations adopting Zero Trust architectures
Service Offerings
Zscaler Posture Control (CSPM & CIEM)
Provides unified CSPM, CIEM, and Infrastructure as Code (IaC) scanning to enforce security policies and compliance.
- Multi-cloud visibility
- Compliance Management
- Risk Prioritization
- Entitlement Management
- IaC Security
Zscaler Workload Communications
Secures cloud workload communications based on Zero Trust principles, contributing to overall governance.
- Microsegmentation
- Identity-based access control
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Custom
Typically priced per user or per workload, depending on the specific services. Contact sales.
Pros
- + Strong Zero Trust architecture integration
- + Unified platform for access, data, and posture
- + Good multi-cloud capabilities
- + Effective risk correlation
Cons
- - May be more focused on network and access security than deep workload internals
- - Platform breadth can mean complexity
Verdict
"A strong contender for organizations committed to a Zero Trust strategy, offering integrated posture management and access controls within its cloud security platform."
Microsoft Azure
Visit Website →Provides native cloud security governance tools tightly integrated within the Azure ecosystem, with increasing multi-cloud capabilities via Azure Arc.
Target Audience
Organizations heavily invested in Azure, Enterprises, Microsoft ecosystem users
Service Offerings
Microsoft Defender for Cloud
Offers CSPM and Cloud Workload Protection Platform (CWPP) features, including security recommendations, compliance monitoring, and threat protection.
- Security posture assessment
- Regulatory compliance dashboard (ISO 27001, PCI DSS, SOC TSP)
- Multi-cloud support via Azure Arc
- Threat detection alerts
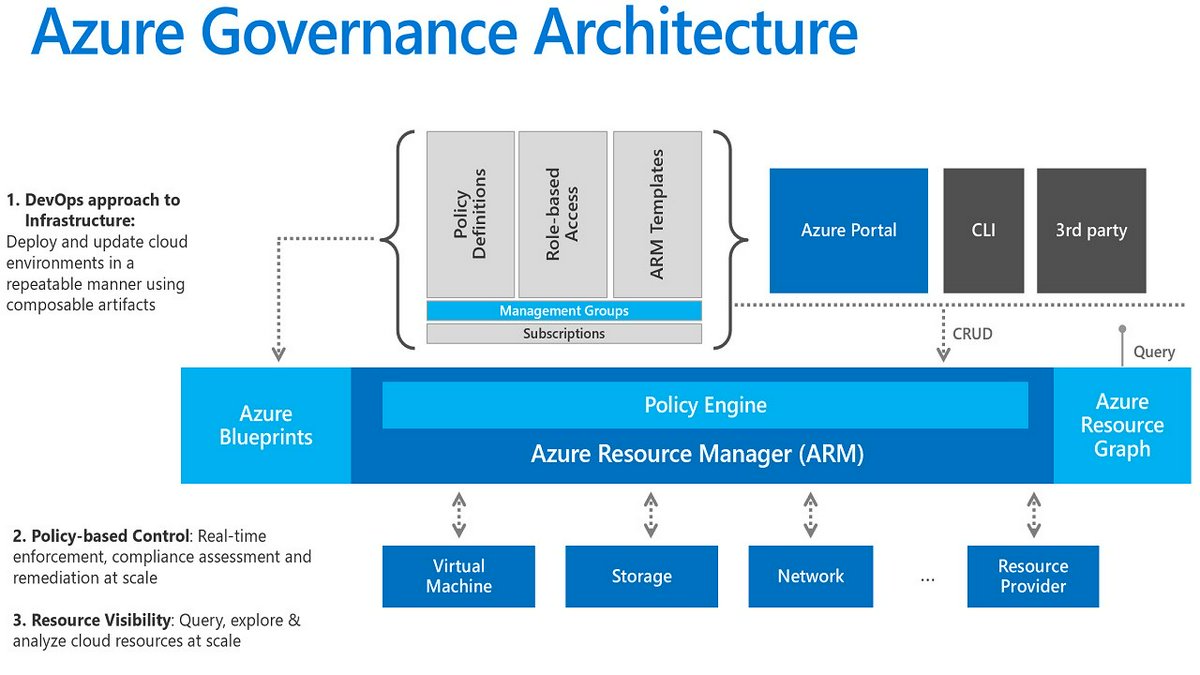
Azure Policy
Enables creation, assignment, and management of policies to enforce organizational standards and compliance.
- Built-in policy definitions
- Custom policy creation
- Compliance auditing
- Automated remediation options
Azure Blueprints
Allows defining repeatable sets of Azure resources that adhere to standards, patterns, and requirements.
- Environment setup automation
- Artifacts like policy assignments, role assignments, ARM templates
Scorecard (Overall: 8.0 / 10.0)
Pricing Model
Usage-based
Many governance features have free tiers; advanced capabilities (Defender for Cloud plans) are often priced per resource or per node. Check Azure pricing calculator.
Pros
- + Deep integration with Azure services
- + Comprehensive feature set within the Microsoft ecosystem
- + Strong policy enforcement engine
- + Leverages broader Microsoft security intelligence
Cons
- - Multi-cloud capabilities still maturing compared to third-party specialists
- - Can be complex to navigate the various interconnected services
Verdict
"The default choice for strong governance within Azure environments, offering deep integration and powerful native tools, with growing multi-cloud reach."
Lacework
Visit Website →Offers a data-driven cloud security platform using behavior analytics and automation for threat detection, configuration monitoring, and compliance.
Target Audience
Enterprises, Mid-Market, Cloud-native businesses
Service Offerings
Lacework Cloud Security Posture Management (CSPM)
Provides continuous configuration monitoring, compliance checks, and reporting across cloud accounts.
- Multi-cloud support (AWS, Azure, GCP)
- Compliance benchmarks (CIS, SOC 2, PCI DSS)
- Risk Prioritization
- Automated Alerting
Lacework Cloud Infrastructure Entitlement Management (CIEM)
Analyzes and manages cloud identities and entitlements to reduce risk.
- Identity and Access Analysis
- Least Privilege Recommendations
Scorecard (Overall: 8.3 / 10.0)
Pricing Model
Custom
Pricing typically based on cloud resources monitored or workload count. Contact sales for details.
Pros
- + Strong automation and behavioral analytics approach
- + Excellent visibility across cloud activities
- + Good multi-cloud support
- + Focus on correlation and context
Cons
- - Newer player compared to some established vendors
- - Can require tuning for anomaly detection accuracy
Verdict
"Ideal for organizations seeking a modern, automation-heavy approach to cloud security governance, particularly strong in identifying anomalous behavior."
Netskope
Visit Website →Provides a cloud-native platform focused on Security Service Edge (SSE) and Zero Trust, including strong CSPM and data governance capabilities.
Target Audience
Enterprises, Organizations focused on data security and SASE
Service Offerings
Netskope Cloud Security Posture Management (CSPM)
Continuously monitors IaaS/PaaS environments for misconfigurations, compliance violations, and risks.
- Multi-cloud visibility (AWS, Azure, GCP)
- Compliance Reporting
- Configuration Drift Detection
- Guided Remediation
Netskope Cloud Data Loss Prevention (DLP)
Extends data protection policies across cloud services, ensuring sensitive data governance.
- Data Discovery and Classification
- Policy Enforcement
- Context-aware controls
Scorecard (Overall: 8.5 / 10.0)
Pricing Model
Custom
Pricing is typically per user per year or based on data volume, varying by modules selected. Contact sales.
Pros
- + Strong focus on data security governance
- + Excellent multi-cloud visibility and control
- + Integrated SSE platform benefits
- + Granular policy engine
Cons
- - Can be perceived as complex initially
- - Primarily focused on data and access paths, less on workload runtime
Verdict
"A top choice for organizations prioritizing data governance and compliance within a broader SASE/SSE framework across multi-cloud environments."
View Top Ranked Provider
Watch a short ad to unlock the details for the #1 ranked provider.
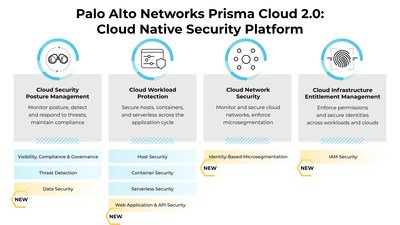
Palo Alto Networks (Prisma Cloud)
Visit Website →Offers Prisma Cloud, a comprehensive Cloud Native Application Protection Platform (CNAPP) providing extensive governance, compliance, and security features across multi-cloud environments.
Target Audience
Enterprises, Mid-Market, Organizations with multi-cloud strategies
Service Offerings
Prisma Cloud Security Posture Management (CSPM)
Provides continuous visibility, compliance monitoring, and threat detection across AWS, Azure, GCP, and other clouds.
- Configuration Monitoring
- Compliance Auditing (NIST, PCI DSS, HIPAA, etc.)
- Misconfiguration Detection
- Automated Remediation Workflows
Prisma Cloud Identity Security
Delivers Cloud Infrastructure Entitlement Management (CIEM) to manage permissions and enforce least privilege.
- Permissions Visibility
- Entitlement Management
- Identity Governance
Scorecard (Overall: 8.8 / 10.0)
Pricing Model
Custom
Pricing is typically based on the number of cloud resources or workloads protected and specific modules purchased. Contact sales for a quote.
Pros
- + Comprehensive feature set across CNAPP
- + Strong multi-cloud and Kubernetes support
- + Robust compliance frameworks and reporting
- + Mature automation capabilities
Cons
- - Can be complex to configure and manage fully
- - Higher price point compared to some competitors
Verdict
"A market leader providing deep, comprehensive cloud security governance capabilities, ideal for complex multi-cloud enterprise environments needing extensive control."

Final Recommendation
The Cloud Security Governance market features comprehensive platforms from specialized vendors and increasingly capable native tools from major cloud providers. Specialized platforms often excel in multi-cloud environments and depth of features, while native tools offer deep integration within their specific ecosystems. Key differentiators include the breadth of CNAPP capabilities, automation sophistication, compliance coverage, and integration with broader security frameworks like XDR or SASE.